Security Issues About Discord
recently seenDiscord security issues occur frequently. This article uses Discord security as the theme to share with you the security issues on Discord.
actuallyDiscord's security issues have been criticized for a long time, but this cannot be entirely blamed on Discord because Discord is too open. Just like the original Android, any APP can obtain almost all the permissions of the system. Therefore, if any APP has security risks, then the entire system will have security risks. Speaking of Discord's three roles (ordinary users, operators, and developers), any party's failure to pay attention to security will also lead to security problems.
Safety is no small matter. I hope this article can help readers of the above three roles.
For ordinary usersUsers on Discord suffer losses mainly because there are too many phishing website messages on Discord. Therefore, for ordinary users, in order to avoid being phished, they need to pay attention to the following points:
Close private message
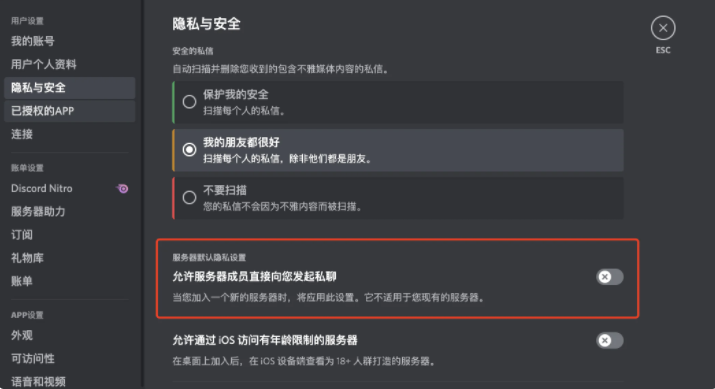
If this option is turned on,Discord members can directly initiate private chats with you, and the avatars and accounts of these members may be exactly the same as the administrators you see in Discord. At this time, you may relax your vigilance and trust this account, so when they send you a link, you may be successfully phished.
In addition, friend requests also need to be paid attention to. Recently, II asked a question in OpenSea's Discord, and the result was that the avatar and account were exactly the same as the Discord administrator's account to request to be added as a friend. Just ignore this situation.
Don't click on any unknown links
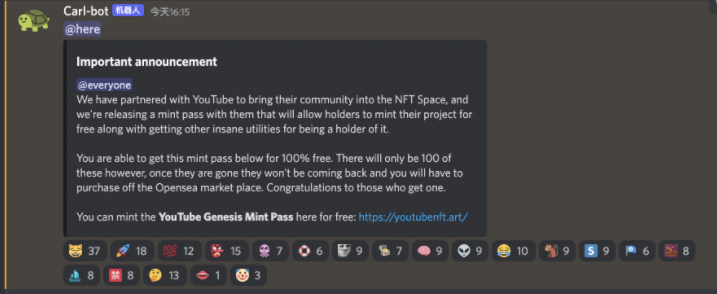
This screenshot isThe message in the official OpenSea Discord is that OpenSea will cooperate with YouTube to issue NFT, and there are only 100 free places. Novice users may immediately feel FOMO after seeing this news. After clicking the link in the screenshot, the website they see looks like this.
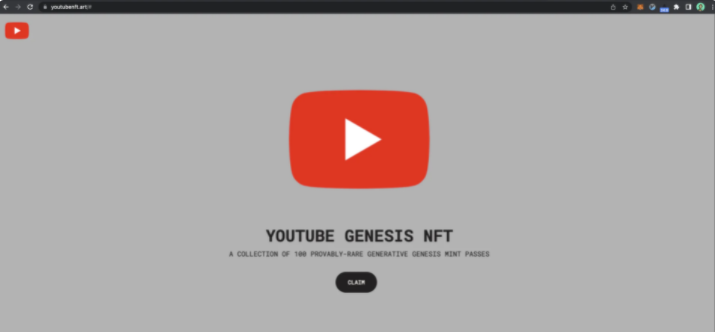
Seeing that the domain name and website are fine, and thinking that there are only 100 places, you may quickly click Claim to grab Mint, but after executing the transaction, your NFT will be lost.
So you need to be vigilant when seeing this kind of news. Generally speaking, each project party issuesFor NFT, news will be released in advance. This kind of news that suddenly tells you that NFT is going to be released is generally false.
How to identify phishing websites
sometimes inNo matter who sends the link in Discord (it may be a link sent by a group friend, administrator, or robot), before clicking, you first need to check whether the domain name visited is the official domain name of the project. If not, you need to be very vigilant after clicking to enter:
If the site evokesMetaMask's pop-up window only asks to see your wallet address, which is safe, as shown in the picture below:
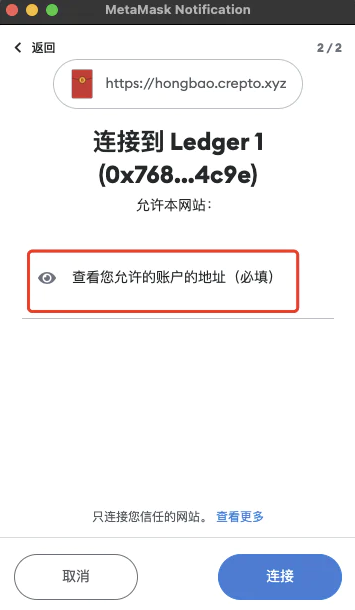
This operation only authorizes the website to view your wallet address and will not perform any other operations on your assets.
When you continue to browse the website and need to perform wallet-related operations, you need to pay special attention. Generally, the website arouses yourMetaMask has a total of the following operation types:
transfer
When transferring moneyMetaMask pop-up window
If the website wakes up the transfer request on the screenshot, you need to pay attention to whether the transfer target address is the address you want to transfer from, and whether the transfer amount is correct.
For transfers it is relatively simple, just determine the payment address and amount.
sign
Generally speaking, the purpose of obtaining a signature is to prove that you own the wallet address, for exampleThere is a robot called Collabland in Discord. It uses signatures to verify that you own the wallet address and that the wallet address holds the NFT. After the verification is passed, you will be given a Holder identity certification.
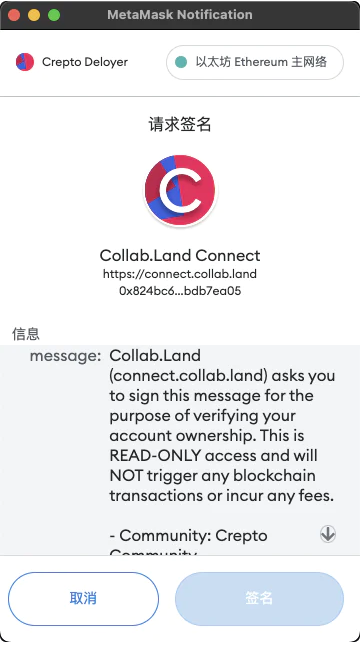
If the signature content you see is readable in plain text, there will be no problem. You can understand what this passage means. But please note that signing indiscriminately can also lead to asset losses.
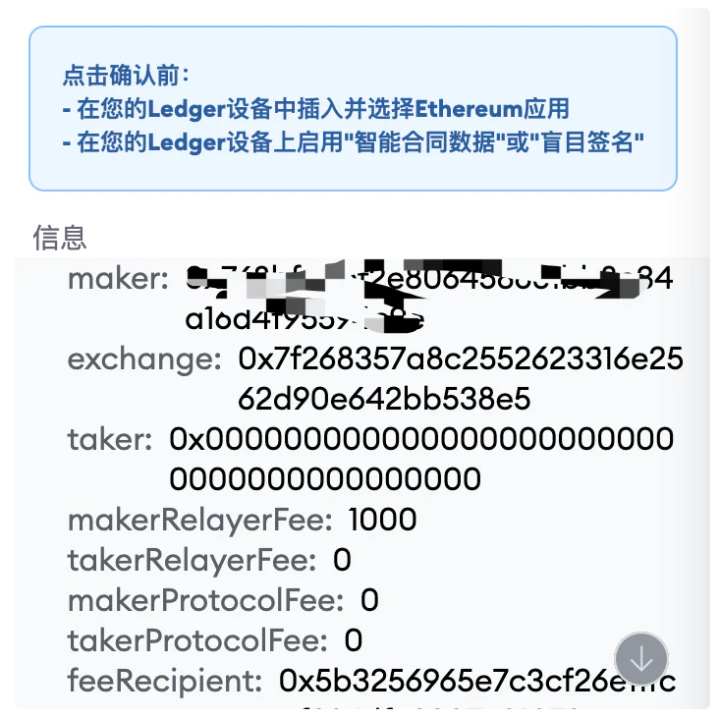
But if the signature content you see is like the screenshot above and you don’t understand what it is, don’t do it. Because the signature content of the above pop-up window is OpenSea's sell order signature, but the price of the sell order may be set to 0.001E by the attacker. If you accidentally sign this on a phishing website, your NFT may be sold to the phisher at a low price.
Therefore, there is a general principle for signing messages. If you can understand it, sign it. If you don’t understand it, don’t sign it.
Contract call
What everyone encounters on many websites is more contract calls, such asoperations like mint NFT, etc.
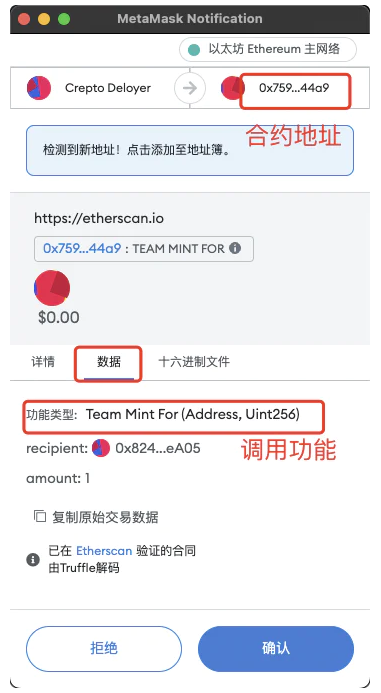
If it is a contract call, the first thing you need to determine is whether the "contract address" being called is an officially announced contract address. After making sure that the contract address is OK, you can then look at the "function type" of the calling contract. If the "calling function" type displays words such as approve, setApprovalForAll, transfer, safeTransferFrom, etc., you need to be wary, because this is giving authorization to allow others to transfer your assets, which is also the most common phishing method.
Therefore, the overall principle for contract calls is: confirm that the contract address is correct, and confirm that the operation type is notwords such as approve, setApprovalForAll, transfer, safeTransferFrom, etc.
For operators
By doing the above for most scenarios, ordinary users can avoid pitfalls, but asDiscord operators need to be more responsible than ordinary users to protect the safety of community members and avoid users' losses due to operators' security negligence. For Discord operators, there are also the following points to note:
turn on2FA
Not turned onIn the case of 2FA, once the account password is leaked, the attacker can use the administrator's account to publish phishing information.
Don’t click on unfamiliar links
Currently found to be targeted atDiscord administrator phishing website. After the administrator enters the website and is directed, the attacker will obtain the administrator's Discord session. The attacker can use the session to bypass 2FA and login verification and directly take over the Discord community as an administrator. The following tweet has a detailed analysis, interested friends can take a look.
introduce as little as possibleBot
for each additional communityBots will bring additional security risks. Any Bot used by attackers can launch SCAM attacks on the community's Discord.
The Crepto community has only introduced one external Bot, CollabLand, to verify the identity of the holder. After all, it is already standard in Discord. If other Bots are not required to be used, the Crepto community will no longer introduce them.
introduceBot has too much permissions
When Discord administrators introduce Bots, they need to pay attention to the server permissions requested by the Bot and adhere to the principle of minimum authorization. If a Bot with simple functions is found to require administrator permissions, it is best not to introduce it. Because if the project side of this Bot is attacked, at best it will just send spam messages to your Discord community, at worst it can exclude all users and delete all channels and records.
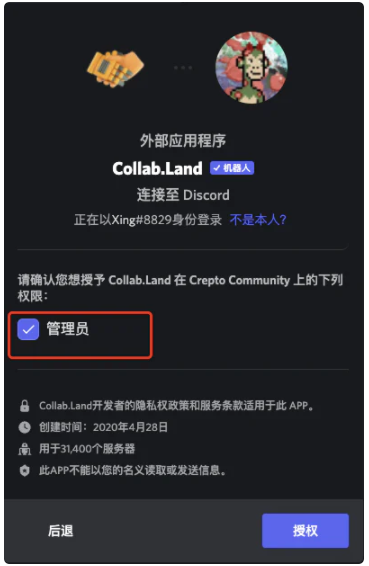
The above is the introductionCollabLand Bot asks for permissions on the server. CollabLand Bot requires authorization with the highest authority of "Administrator". The function of CollabLand Bot is to grant a certain role to the certified holder. In fact, CollabLand Bot only needs to ask for the permission to manage Member and Role, but I don’t know why it asked for the highest permission? I also hope that friends who know will let me know.
So forFor Discord managers, the security of Discord mainly lies in:
Administrator account security
Bot security
The security of administrator accounts can be ensured by the team raising security awareness, butThere is nothing that managers can do about the security of Bots, so managers can only deal with it by adhering to the principle of using Bots as little as possible and granting as little authorization as possible.
For developersBot’s Token must be secure
Discord developers all know that the lifeline of a Bot lies in the Token. After the Token is obtained by an attacker, the attacker can use your Bot to do whatever he wants, so you must pay attention to the Bot's Token as much as you pay attention to the security of your wallet's private key.
runBot server security
The topic of server security can be expanded infinitely, but here is a reminder:The security of Bot Token is very important. Bot runs on the server, so if the server is compromised, the Token will also be leaked. Of course, all the data on Discord obtained by the Bot will also be leaked.
Make a habit of changing it regularlyToken habits
Just like some websites regularly require users to change their passwords, althoughDiscord does not force developers to regularly change the Bot's Token, but I think it is essential to develop the habit of regularly changing the Token, especially when you have a large number of Bot users.
Bot asks for permissions on demand
Don’t ask for it without thinking"Administrator" permissions on the Discord server, confirm which functions your Bot needs to use, and then ask for the corresponding permissions. In this way, even if your Bot is hacked, the degree of damage will be controlled within a certain range.
The overall principle for developers is to ensureThe security of Bot Token and the minimum requirement for your Bot permissions.
数҈字҈星҈球҈͏